Fixing security threat with post
- ICDesign
- 2023-09-23 23:01:40
One of the most critical ramifications of the emergence of quantum computers is the impact on security because quantum computers have the potential to break even the most secure encryption methods used today. That is why the industry will be seeing a rapid shift from traditional cryptosystems to Post Quantum Cryptography (PQC) systems in the next few years. PQC systems respond to this growing quantum threat because they are based on mathematical problems that cannot be solved efficiently with Shor’s algorithm, or by any other known quantum computing algorithm.
In this article, we’ll explain how companies can start building PQC security into their computers and network equipment today by leveraging embedded FPGA (eFPGA) that can be easily updated in the future as the threat of quantum computer security attacks become a reality. But first, let’s take a look at what this threat is and why every system-on-chip (SoC) or systems designer should be taking it seriously.
How quantum computers break security algorithms
Today’s cryptosystems leverage asymmetric cryptography algorithms that are used by modern security protocols for key exchange and digital signatures that rely on the complexity of certain mathematical problems. Currently, the main problems used for asymmetric cryptography are integer factorization of the RSA algorithm and discrete algorithm of the elliptic curve cryptography (ECC). Shor’s algorithm is a quantum algorithm that can solve these problems on a large enough quantum computer. If this happens, cryptosystems utilizing RSA and ECC would be compromised.



One of the biggest misconceptions is that companies don’t have to worry about this right now because quantum computers big enough to break modern-day cryptosystems don’t exist today. This is not the case because many semiconductor chips being designed today will still be in use for decades. It means that when quantum computers become mainstream, all the data on all those semiconductor chips instantly becomes at risk. Yes, even data recorded today could be broken into in the future when a powerful-enough quantum computer comes along.
The rise of PQC
Recognizing the need to mitigate the risk of quantum computers, the National Institute of Standards and Technology (NIST) of the United States initiated a competition in 2016 to find solutions to standardize PQC algorithms. After three rounds that concluded in July 2022, four candidate algorithms were selected for standardization: CRYSTALS-Kyber, CRYSTALS-Dilithium, Falcon, and SPHINCS+. Kyber is a so-called Key Encapsulation Mechanism (KEM) that is used for key exchange and the rest are digital signature algorithms.
NIST continues the competition with a fourth round to find even further advanced PQC algorithms for a more robust standard in the future. Although the algorithms to be standardized are now known, they may still be tweaked before even the draft standards are written. The final standards are expected to be published in a couple of years and may still change from what is known today.
However, even though these algorithms have been selected, the standards are not yet finalized even though there is an urgent call for systems designers to start migrating to PQC immediately. In fact, many organizations are starting to mandate that security systems support PQC in the near future. As an example, the National Security Agency (NSA) has mandated that certain U.S. national systems must support PQC in 2025. These requirements, combined with the still changing PQC landscape, set very high needs for crypto agility: the ability to update and change cryptographic algorithms in deployed systems.
To trust or not to trust
Because PQC schemes are only a few years old and many are based on new types of mathematical problems, they cannot be fully trusted at this stage or even when the final standards are out. It’s entirely possible that previously unknown weaknesses will be discovered and allow breaking them even with classical computers.
To mitigate the risks of a failure of the new PQC schemes, many authorities, researchers, and security professionals recommend using a hybrid mechanism. A hybrid mechanism combines a PQC scheme with a traditional scheme—ECC in most cases—so that the combination remains secure even if one of them fails under classical or quantum attacks.

Figure 1 Security professionals increasingly recommend hybrid mechanisms that combine PQC with traditional schemes like ECC. Source: Flex Logix
Hybrid mechanisms will reduce both risks: the quantum threat and the possible failure of PQC. It is likely that hybrid mechanisms will be widely deployed and used for a long time. This sets high requirements for the implementation of secure systems, as they need to have secure and efficient implementations of both ECC and PQC. They must also be implemented in a crypto-agile manner that permits changes after deployment if some of the algorithms are upgraded or replaced. This is a challenge that reconfigurable computing can answer.
How eFPGAs can help
The problem both SoC and systems designers have today is how to start incorporating PQC support even though the PQC algorithms may change in the next several years. This is a big problem with current chip design because chip circuitry typically cannot be changed or modified after tape-out. And with the rapidly rising cost of developing SoCs, particularly at advanced process nodes where a spin or re-spin could take millions of dollars, there is not an easy solution. Or is there?
Here, at this security technology crossroads, eFPGAs are uniquely qualified because they provide the ability to change the PQC algorithms while still providing the performance and power and cost savings over other alternatives. It’s also possible to retro fit PQC into systems that already have eFPGA included in the SoC. In addition, by adding reconfigurable computing to the SoC, the system can save on power and cost yet still have high-performance encrypting.
Using eFPGA, chip designers are no longer locked in once RTL is frozen, but rather have the flexibility to make changes at any point in the chip’s life span, even in the customers’ systems. This eliminates many expensive chip spins and enables designers to address many customers and applications with the same chips. It also extends the life of chips and systems because designers are now able to update their chips as protocols and standards change in the future.

Figure 2 eFPGAs are uniquely qualified for applications like PQC support in SoC designs. Source: Flex Logix
Many existing SoC architectures have hardened cryptography modules that include support for a multitude of cryptography algorithms including ECC, but not PQC. Updating these modules to support PQC and hybrid mechanisms after deployment is very hard or even impossible and very expensive without eFPGA. Cryptography modules with PQC support will be difficult and risky even in new projects in the future as they may not be available in the market at all or come with fixed parameter sets that are impossible to change if the algorithms get tweaked in the final stages of the PQC standardization process or even broken later. Here, eFPGA permits complementing cryptography modules with PQC support that can be updated to accommodate any future changes.
eFPGA may be used also for implementing the entire hybrid mechanism in a resource efficient manner. eFPGA can be first programmed to implement a PQC KEM and to compute the PQC shared secret, next to implement ECC and to compute the ECC shared secret, and finally programmed to implement the key derivation function that computes the final shared secret from the PQC and ECC shared secrets.
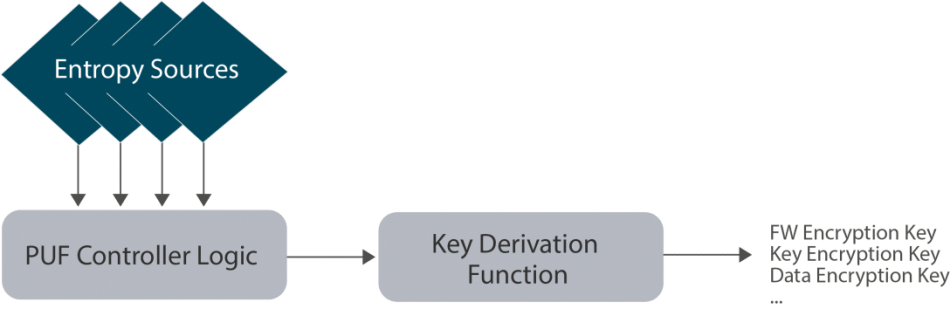
An eFPGA inside the SoC allows for other advantages besides being smaller and generating less heat. One of the problems facing cryptographers is the issue of export laws of various countries and the issue of sensitive information being provided to nefarious people who wish us harm. With an eFPGA inside the SoC, the PQC algorithms remain safe by programming after the SoC is back from manufacturing in a known safe location. The eFPGA binaries can be encrypted using physically unclonable function (PUF) to further secure them in case the computing device is stolen or lost in the field.
Are your systems ready?
While the age of quantum computers has not yet been realized, this threat is coming sooner than people think. Systems designers need to protect not only the data they are recording today, but their data of the future. An SoC manufacturer that can provide the assurance that its SoC today will be able to adapt to changing protocols and threats in the future will be the clear winner.
Andy Jaros VP of sales at Flex Logix.
Kimmo Järvinen is CTO and co-founder of Xiphera.
Matti Tommiska is CEO and co-founder of Xiphera.
Related Content
Closing Knowledge Gap on Hardware SecurityThe Role of Hardware Root of Trust in Edge DeviceseFPGA expands the ecosystem footprint one deal at a timeEmbedded FPGA (eFPGA) technology: Past, present, and futureWhat’s Driving the Shift from Software to Hardware in IoT Security?Fixing security threat with post由Voice of the EngineerICDesignColumn releasethank you for your recognition of Voice of the Engineer and for our original works As well as the favor of the article, you are very welcome to share it on your personal website or circle of friends, but please indicate the source of the article when reprinting it.“Fixing security threat with post”