Ascon algorithms finalized for lightweight cryptography
- Sensors
- 2023-09-23 23:31:32
The National Institute of Standards and Technology (NIST) has selected a group of cryptographic algorithms to secure the Internet of Things (IoT) devices and the related tiny sensors and actuators. Ascon, a group of cryptographic algorithms, will also serve other miniature devices like medical gadgets, stress detectors inside roads and bridges, and keyless vehicle entry fobs.
NIST will publish the “lightweight cryptography” standard later this year. It’ll be targeted at tiny devices that have limited resources and thus demand a compact security implementation. “The Ascon algorithms for lightweight cryptography will cover devices with resource constraints,” said NIST computer scientist Kerry McKay.
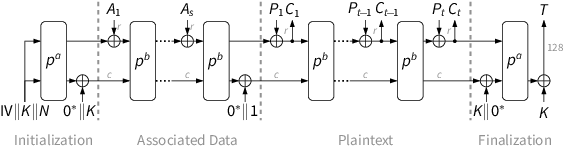
Figure 1 Ascon algorithms have withstood years of examination by cryptographers. Source: Ascon



Several years ago, NIST announced a development program to determine the strongest and most efficient lightweight algorithms, first communicating with industry and other organizations to understand the needs. In 2018, it requested potential solutions from the cryptography community and received 57 submissions. Next, McKay and mathematician Meltem Sönmez Turan carried out a multi-round public review process and selected 10 finalists.
Finally, Ascon became the winner for its algorithm’s performance and flexibility in terms of speed, size, and energy use. Ascon—developed in 2014 by a team of cryptographers from Graz University of Technology, Infineon Technologies, Lamarr Security Research, and Radboud University—is currently available in seven variants.
Ascon’s lightweight cryptography variants
According to McKay, Ascon’s two variants or tasks are among the most important in lightweight cryptography: authenticated encryption with associated data (AEAD) and hashing. AEAD—besides protecting the the confidentiality of a message—allows additional information like the header of a message or a device’s IP address to be included without being encrypted. In lightweight cryptography, it can be used in vehicle-to-vehicle communications. It can also help prevent the counterfeiting of messages exchanged with the RFID tags that often help track packages in warehouses.
On the other hand, hashing creates a short digital fingerprint of a message that enables a recipient to determine whether the message has changed. It can be used to check whether a software update is appropriate or has been downloaded correctly.
Here, it’s worth mentioning that the the most efficient NIST-approved technique for AEAD is the Advanced Encryption Standard (AES), while SHA-256 is widely used for hashing. However, as McKay clarified, the goal of this project is not to replace AES or hash standards. “NIST still recommends their use on devices that don’t have the resource constraints that these new algorithms address.”

Figure 2 Lightweight cryptography serves small devices for tasks ranging from sensing to identification to machine control. Source: NIST
McKay added that the new algorithms are also not intended to be used for post-quantum encryption, another current concern of the cryptography community that NIST is addressing. “Post-quantum encryption is primarily important for long-term secrets that need to be protected for years,” she said. “In contrast, lightweight cryptography is generally important for more ephemeral secrets.”
Related Content
Are you prepared for zero-day threats?Closing Knowledge Gap on Hardware SecurityEnding the Cat-and-Mouse Game of Firmware AttacksWhat’s Driving the Shift from Software to Hardware in IoT Security?The Unexpected Outcome of Ransomware: An Industrial Digital RevolutionAscon algorithms finalized for lightweight cryptography由Voice of the EngineerSensorsColumn releasethank you for your recognition of Voice of the Engineer and for our original works As well as the favor of the article, you are very welcome to share it on your personal website or circle of friends, but please indicate the source of the article when reprinting it.“Ascon algorithms finalized for lightweight cryptography”